How to start protecting your business!
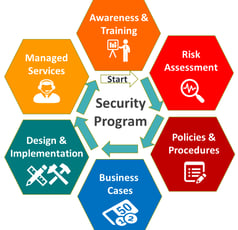
The first step of protecting your small business or home is figuring out what you need to protect the data you have and what you have in place and how those things work together to protect you.
Step one: Meet with a cybersecurity consultant.
In this step you will schedule a FREE (that's right FREE!), cybersecurity consultation with me. We will sit down (virtually), and address your concerns, what you have implemented and where you would like to be.
After we discuss that and I give you some recommendations you can choose to either do it all on your own or allow Link-IT Solutions to help relieve that stress for you!
Step two: Figure out the data that needs protecting
Every business deals with different type of data. From public to private, internal to external, and regulated to non regulated. We will discuses what data you are most worried about protecting and which of that data (if any) has any federal regulatory requirements surrounding the protection of it.
Step Three: Conduct a Cyber Risk Assessment to determine Vulnerabilities
Once we determine the type of data we are protecting, we will do a deep dive into your network, endpoints, devices, and policies to see what security measures are already in place and where we can improve. This can cover anything form ensuring default passwords are not used to implementing Endpoint Detection and Response on your computers and mobile devices.
Step Four: Determine the Risk to your Business
After determining the vulnerabilities with the Cyber Risk Assessment. We will discuss how and determine the risk to your business should the worst happen. We will touch on many topics including, insider threats, employee mistake, natural disasters and everything and anything else we can think of. We will also discuss the likeliness of each factor happening and what are the consequences if it does.
Step Five: Create a Plan!
In this step, you as the business get to see the ways we can make your business even more secure than it was! In this plan, we take everything we learned in steps three and four and create a roadmap of issues we can address.
This plan will cover everything from the specific type of data you are protecting, to computer security, mobile security, facility security, and the all important Employee Training!
Step Six: The Roadmap to Success!
Finally! You have made it to the part where we make all of this actually real. Through a series of virtual meetings, We work together to implement the changes we have identified for your business. In this step, we will go as fast or as slow as you need and times that fit in with your schedule.
Step Seven: Create and Sign Policies
In this step, Ill provide you polices that may be required by regulations. These policies will help protect the company in the future.
Step Eight: Training, Yay!
Nothing works well unless people are trained correctly. It has been determined that most cyber attacks occur in some sort of social engineering campaign. I will assist in training your employees Quarterly, Monthly, or whatever cadence you feel is important for your business. This training will touch on, security awareness, new policies, security "best practices", phishing awareness, or any other cyber training you may feel your company needs.
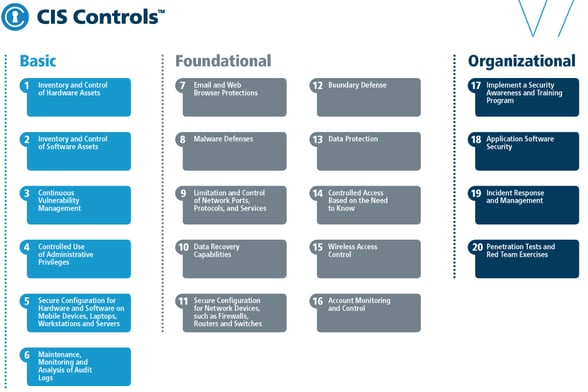
What the heck is CIS Controls and framework??
The CIS (Center for Internet Security) Controls Framework is a set of best practices that organizations can follow to enhance their cybersecurity posture. It provides a systematic approach to identify, mitigate, and manage cyber risks effectively. The framework consists of 20 security controls, which are prioritized based on their effectiveness to address common cyber threats. These controls cover various aspects of cybersecurity, including inventory and control of hardware and software assets, continuous vulnerability management, secure configuration for hardware and software, and incident response planning. By implementing the CIS Controls Framework, organizations can establish a strong foundation for their risk assessment activities. It helps them identify and prioritize potential risks, implement appropriate safeguards, and continuously monitor and improve their security measures. Ultimately, using the CIS Controls Framework ensures that organizations are well-prepared to mitigate cyber risks and protect their valuable assets.